android overlay target что это
‘SAW’-ing through the UI: Android overlay malware and the System Alert Window permission explained
Over the past month, we’ve talked about a troublesome Android app permission called `SYSTEM_ALERT_WINDOW` a couple of times in our weekly #MobSec5 news digest — subscribe here. This week, researchers from University of California Santa Barbara and Georgia Institute of Technology released details about “Cloak and Dagger” a collection of attacks that take advantage of this permission. Customers 1 have asked me about `SYSTEM_ALERT_WINDOW` (abbreviated SAW for the purposes of my oh-so-witty headline) a nd how malware might abuse the Android overlay view to steal log-in credentials and the like from Android users. I wanted to explain the Android app permission in plain language, how it might be abused, and finally what people can do to mitigate the risk.
What is Android screen overlay and what’s it for?
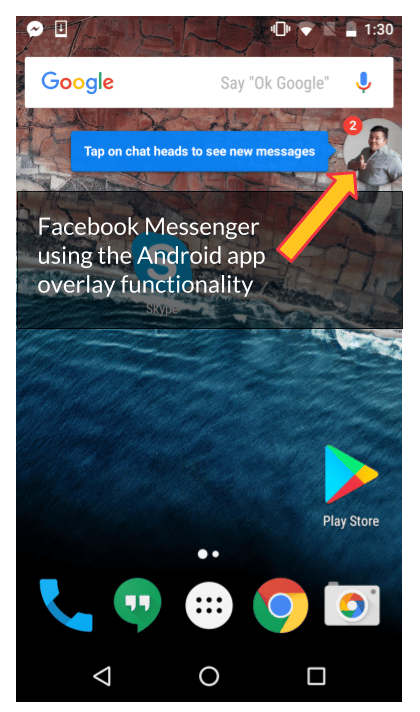
A screen overlay in Android, also referred to as “Draw On Top”, allows an app to display content over another app. The Android app permission SYSTEM_ALERT_WINDOW makes this possible. If you’ve ever used an app like Facebook Messenger or Lastpass, you’ve experienced screen overlay in action. Basically, the permission allows a developer to display content on the screen of your Android device after some trigger event.
For example, you may have seen the cute notification bubble in Facebook Messenger (also called a “chat head” — see the screenshot above) that includes a contact’s photo. If you tap the chat head, it leads to a pop-out version of the Messenger app. Have you noticed that you never gave Facebook Messenger permission to display that bubble?
The System Alert Window Android App Permission
This blows my mind, because if someone were so inclined, they could potentially compromise a user’s phone with the SYSTEM_ALERT_WINDOW permission using Android overlay malware. Overlay malware is not a new concept, and the Google Play Store has published a number of malicious apps that abused the Android screen overlay. The apps typically pose as something harmless. In one example of Android overlay malware discovered by ESET, a malicious flashlight app actually turned out to be banking trojan malware.
Potential abuses of the System Alert Window permission
Generally, these attacks play out something like this
The SYSTEM_ALERT_WINDOW permission makes a number of attacks possible, but overlay attacks seem to be the most prominent at this time. Once a malicious app has been installed on your device, the app will wait for the user to launch a target app. When the target app is launched, the malicious app produces an overlay to trick users into entering their credentials into a phony login screen. The user’s credentials are then sent to the attacker’s server.
The animation below demonstrates what an attack might look like on a victim’s phone. You can find the sample malware I used for the demonstration on Github: https://github.com/geeksonsecurity/android-overlay-malware-example.
Here’s what you’re seeing in the video:
Android overlay attacks and ransomware
With ransomware concerns rising in the wake of the WannaCry attack earlier this month, there have been some suggestions that overlay screens could be used to launch a ransomware attack on Android devices. This is pure speculation, but malware could potentially display an overlay screen demanding credit card information to make it go away. It’s possible some users will fall for the ploy when in reality their files weren’t encrypted or inaccessible and they could have exited the app via other means.
Also of concern is that nothing currently indicates to an app that another app is overlaying its UI. And this may be possible via apps published on the Google Play store, not a third party app store. While it might be tempting to call this a bug that can be patched, it seems like a fundamental flaw in Android’s permissions design.
How can I protect myself against abuse of the System Alert Window permission?
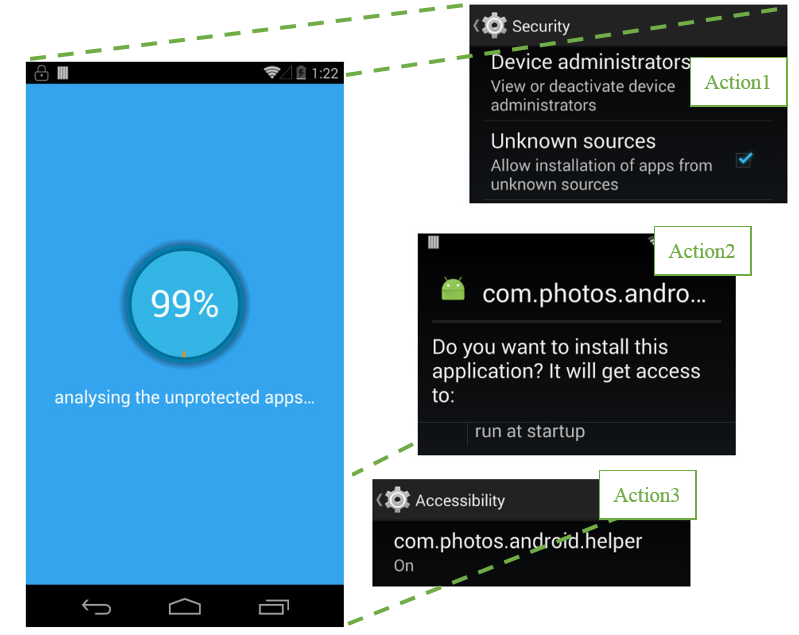
Some of the most popular apps on the store call on the SYSTEM_ALERT_WINDOW — not just malware. Users can see what apps have the permission using the instructions in the table below (instructions may not apply to all devices).
| Version | How to review apps with Draw Over Other Apps permission |
|---|---|
| Android 7 | Settings > Apps > “Gear symbol” > Special Access > Draw over other apps |
| Android 6 | Settings > Apps > “Gear symbol” > Draw over other apps |
| Android 5 | Settings > Apps > Select app and look for “draw over other apps” |
In addition, before downloading an app, you can check to see if the app uses the `SYSTEM_ALERT_WINDOW` permission by reading the “Permission Details” on the app’s page in the Google Play Store and looking for a “draw over other apps” bullet.
What makes these `SYSTEM_ALERT_WINDOW`-based attacks so scary is Google’s app vetting process has failed to identify a few of these apps before they’re published on the public app store. Google has, however, started tackling this issue in Android O. There are reports that the beta version of Android O includes a mechanism that will notify users that app overlay is taking place. While this is a step in the right direction, Google might need to consider treating the overlay permission in the same way it treats camera permissions. Still, users stuck on older versions of Android could still fall victim.
1 Special thanks to Dan Dumitrescu, security specialist at a financial institution.
What to read next:
Mobile banking Trojans: What can financial institutions do?
A seeming resurgence in mobile banking Trojans has financial institutions asking questions. NowSecure CTO David Weinstein has answers.
[Советы] «Липосакция» Android + MIUI 10 или отключаем ненужное
| [index]Содержание [#1]Общее… [#2]Список замороженного с пояснениями [#3]Скрипт для отключения замороженного [/index] |
Рад всех приветствовать!
Хотел рассказать о своём опыте облегчения жизни устройству, заключающееся в отключении мне не нужных приложений, сервисов и т. п.
Возможно, кому–либо это поможет.
Пост постараюсь поддерживать в актуальном состоянии. С задержкой от «нововведения» минимум на сутки, так как надо сначала самому оценить влияние любого, вновь отключаемого приложения, а уж потом писать.
Правда, приходится не забывать запускать его каждый раз при перезапуске аппарата, так как с редактированием init.qcom.rc и (или) default.prop у меня лёгкая проблема в виде бутлупа 🙂
А дальше итерационно…
В Titanium Backup приложение морозится, удаляются его данные. Перезагрузка в TWRP, Очистка → Выборочная очистка → Dalvik/ART cache + cache → перезагрузка в ОС, ожидание, Titanium Backup, …
На следующей странице (оглавление вверху) что было заморожено с пояснениями по поводу приложений (что знал и удалось найти в сети). Удалил без сожаления facebook, MGRSVendorApp, PartnerNetflix…
Установщик пакетов из GApps’ов ( com.google.android.packageinstaller ) удалять нельзя! Морозить тоже. Будет лёгкий кирпичик. Скорее всего, возврат /data/system/packages.xml проблему решит, но не факт.
На текущий момент мой R5A жив-здоров и за весь день (05:00 ÷ 21:00) съедает 20 ÷ 25 процентов заряда (по данным BetterBatteryStats до 1,6%/час), и это за рабочий день, когда звонки, СМС и почта + нет WiFi, LTE не работает и сидишь на 3G. Сейчас суббота, за 16 часов при подключенном WiFi расход 10 (десять) процентов батареи. Как по мне вполне хороший результат. Некоторые приложения ругаются на то, что им нужны google play services (штатный ассистент, музыка, Авито, Вайбер), но при этом вполне себе работают и не докучают вылетами. На четвёртой странице скриншоты… Они местами длинные очень И на экране компа смотрятся непривычно.
Чтобы на 10.1.1.0.NCKMIFI нормально работал TitaniumBackup до первого использования стоит поставить busybox. До этого я голову себе сломал, пытаясь понять почему же не все версии запускаются (особенно новые).
NB! После проведённых манипуляций аппарат до заводских настроек не возвращается. Только полная перепрошивка. Связано это с ГАппсами, насколько я смог понять.
«The Compatibility Test Suite (CTS) is a free, commercial-grade test suite, available for download. The CTS represents the «mechanism» of compatibility.
The CTS runs on a desktop machine and executes test cases directly on attached devices or an emulator. The CTS is a set of unit tests designed to be integrated into the daily workflow (such as via a continuous build system) of the engineers building a device. Its intent is to reveal incompatibilities early on, and ensure that the software remains compatible throughout the development process.»
«CTS uses these apps to test privileges and permissions. To pass the tests, you must preload the apps into the appropriate directories on the system image without re-signing them.»
Android-приложение поверх других приложений
В 2013-году Facebook выпустил функцию Chat Heads для своего мессенджера, который позволяет вести переписку, не открывая сам мессенджер путем нажатия на маленькое круглое окошко, которое всегда висит на дисплее даже поверх других приложений:
Facebook одним из первых продемонстрировал реализацию «Drawing over other apps». Данную возможность разработчики сейчас используют в различных типах приложений — от боковых смарт-меню до записи экрана. В этой статье, хочу продеменстрировать процесс написания приложения-поверх-других-приложений на примере «анти-шпионской» программы Khameleon.
Для начала обозначу цели приложения, который будет реализован как пример приложения-поверх-других-приложений. Допустим нужно, чтобы рядом стоящие люди не могли с легкостью видеть контент моего смарфтона, пока я им пользуюсь. То есть необходима возможность:
С функционалом приложения определились — теперь приступим к самому туториалу. Для написания приложения-поверх-других-приложений есть две самых главных составляющих:
А для API > 23, т.е. Android M, нужно запросить разрешение в главном Activity:
После того как разрешение получено, укажем Layout, который нужно отобразвить на экране (многие элементы убраны для демонстрации):
В корневой RelativeLayout (по вашему усмотрению) можно поместить любые View’шки как обычно. View с нам нужен для того, чтобы показать как динамично менять размеры Layout. То есть через эту View’шку можно будет расстягивать и сжимать корневой RelativeLayout.
Как только у нас есть минимальный Layout, необходимо реализовать самый обычный Service. Единственная особенность сервиса в добавлении ранее созданного Layout:
На данном этапе наш Layout успешно отображается поверх других приложении. Теперь рассмотрим как можно динамично менять размеры нашего Layout:
Если потянуть за край Layout вверх или вниз, его высота соответственно сжимается и расширяется.
Мы рассмотрели минимальные необходимые шаги для написания приложения-поверх-других-приложений. Полный код для приложенения Khameleon, продемонстрированный выше, можно найти здесь.
Найдена первая малварь для Android, атакующая пользователей через Toast-уведомления
Реверс малвари
В сентябре 2017 года специалисты компании Palo Alto Networks рассказали об интересной технике атак, на создание которой их вдохновила другая проблема Android-устройств, носящая поэтичное название «Плащ и кинжал». Тогда эксперты Palo Alto Networks предложили концепт атаки, которая основывается на эксплуатации всплывающих уведомлений (Toast messages). Обычно такие сообщения «живут» совсем недолго и появляются внизу экрана устройства. Эти быстро исчезающие уведомления используются многими приложениями, к примеру, Gmail подтверждает таким способом отправку писем.
Такие уведомления появляются поверх окон любых приложений, и для этого даже не приходится задействовать функцию Draw on top. По сути, атакующему достаточно убедить жертву установить вредоносное приложение. Затем злоумышленник может запросить правда администратора или доступ к Accessibility service, но эти запросы будут подаваться жертве как кастомные всплывающие уведомления (за которыми на самом деле будут скрываться кнопка). Специалисты Palo Alto Networks отмечали, что появление таких уведомлений можно зациклить, то есть маскировка преступников может держаться столько, сколько потребуется.
Данная проблема получила идентификатор CVE-2017-0752 и была официально устранена в том же месяце. Но, к сожалению, экосистема Android по-прежнему сильно фрагментирована, то есть множество устройств не получили и никогда не получат патча для описанной проблемы. А концепт атаки, придуманный специалистами, не могли не заметить злоумышленники.
Специалисты компании Trend Micro сообщили, что им удалось обнаружить первую малварь, которая использует Toast Overlay для атак на практике. Вредонос получил имя ToastAmigo и был найден в составе двух приложений в официальном каталоге Google Play. Оба вредоносных приложения назывались Smart AppLocker и позволяли задать PIN-код для запуска отдельных программ на устройстве.
После запуска зараженного приложения, ToastAmigo инициировал атаку с использованием всплывающих уведомлений, отображая огромное уведомление, закрывающее весь экран и демонстрирующее фальшивый интерфейс приложения. На самом деле под этой фальшивкой скрывались запросы на получение доступа к Android Accessibility. Обманутые пользователи полагали, что нажимали на кнопки интерфейса, но на самом деле лишь выдавали новые права малвари.
Если атака удавалась, ToastAmigo устанавливал на устройство еще одно приложение, которое исследователи назвали AmigoClicker. Данный вредонос – это обычная адварь, которая устанавливает прокси и загружает рекламу, принося своим операторам финансовую выгоду. Однако также AmigoClicker способен собирать информацию об аккаунтах Google, нажимать на кнопки в системных диалогах, скликивать рекламу в Facebook, а также оставлять самому себе положительные отзывы в Google Play.
В настоящее время оба вредоноса уже удалены из официального каталога приложений.
[Update:1] Power apps & tweaks for non-rooted devices
Breadcrumb
evanB70
Senior Member
ADB is an immensely powerful tool & it allows you to do a lot of things that would otherwise require root. Today I’m going to share some of the tweaks I use on my device and the best part is, none of these requires root access. This is a post for non-experienced android users. The tweaks / apps discussed here should work on all Android devices.
This post took a looong time to compile. It’s a work-in-progress; I do have some more ADB tweaks in mind; but I have to test them myself before posting them here. I’ll update this post with relevant screenshots soon. So stay tuned and hit the Thanks button if you think this post is useful.
For the content ahead, I’m going to assume you have ADB installed on your PC. Always use the latest version of ADB; some commands won’t work with older ADB binaries. You can grab the latest version of platform-tools from HERE, directly from Google. If you want to learn how to setup & run adb on your PC, take a look at the first part of THIS article.
1. Debloat your device: Remove & disable unwanted system apps
2. Freeze Any App’s Background Processes
3. System-wide Ad-blocking without using any apps
4. Use Android 10’s native gesture navigation with any 3rd party launcher
5. Change the height of the navigation bar
6. Add Left/Right Keyboard Cursors to the Nav Bar during Text Input
7. App: Greenify
8. App: Quick Settings
9. Stop Vibrations from Any Android App on Your Phone
10. Advanced app permission management with Shizuku & AppOps
11. Control your phone from your PC
12. Advanced device stats & hardware monitoring: coming soon
13. Backup your apps+data with ADB: Needs testing, coming soon
1. Debloat your device: Remove & disable unwanted system apps
Removing system apps with ADB is very easy & safe. It doesn’t modify your system partition, so OTA updates are not affected. There is a very easy to follow guide available on XDA about this, click here to read that post. I’ll just mention the commands here:
’ with the actual package name of your target app. You can use a tiny app called App Inspector from the Google Play Store to find out the package name of your target app. You can also use the following adb command to list all the app packages on your device, including system apps:
Warning: Do NOT disable/uninstall Quickstep, Android’s built-in launcher. A10’s stock gesture navigation is an integrated part of this launcher. If you disable/uninstall it, your phone will continue to function but stock gestures won’t work anymore & the recent apps switcher button on your navbar will stop functioning. The good news is, it’s possible to reinstall the launcher using the reinstall command given below.
To Re-Install an Uninstalled App, open a command prompt and enter the following command:
Here is a list of package names of all stock apps for MI A3, as requested by @pajos.gabros:
(it will be useful if you mistakenly uninstall an important system app & want to restore it)
I’ve uninstalled a lot of pre-installed apps using this method, so far so good. No issues whatsoever. However, your mileage may vary, backup your important stuff first. Don’t just start removing apps blindly; If anything goes wrong try to reinstall it with the given ADB command. If that fails, do a factory reset.
I can’t be held responsible for any sort of damage.
Here is a list of apps that I’ve uninstalled (I’ve included the full ADB command, just copy & paste):
Note: You might want to keep some of the apps marked with an asterisk (*)
Note: You can also disable an app if you don’t want to uninstall it. Use the following command:
Here is a list of apps I’ve disabled with no side effects (again, your mileage may vary):
2. Freeze Any App’s Background Processes
There is an article on XDA on this subject, click here. From the article:
‘A simple trick you can do to manually prevent an application from ever running in the background – and it doesn’t require root or a third-party application. This is more powerful than what Greenify or apps like Brevent offer, as without root access those apps are fairly limited in what they can do. But with this trick, now you can block apps such as Facebook or Hangouts from ever running in the background – they will only work when they are actively being used!’
Okay, follow the article if you want to know more. I’m just sharing the commands here:
’ with the actual package name of your target app.
3. System-wide Ad-blocking without using any apps
Google introduced Private DNS mode with Android 9, making it very easy to use a custom DNS provider. You can block ads using a DNS provider that supports AdBlock. I use AdGuard. These days free apps are riddled with full-screen ads & I haven’t seen a single ad on any app after switching to this service. Still, DNS based ad-blocking may not be 100% reliable all the time (It hasn’t failed me yet), so for best results, use AdGuard DNS with a browser that also supports ad-blocking, such as Brave, Bromite, Firefox with uBlock Origin etc.
To setup AdGuard DNS, go to:
Settings → Network & internet → Advanced → Private DNS
Now, select the Private DNS provider hostname option & enter:
To make sure your DNS is properly configured, visit this page, scroll down a little & it should say “You are using Default AdGuard configuration”
Note: Let me make this clear. AdGuard is a Russian service. That does NOT make it less trustworthy by default IMHO, but If you decide to use their service, you’re basically giving them a complete log of every site you visit on the internet. However, it’s the only mainstream DNS provider I could find that supports blocking ads. Make your choice.
4. Use Android 10’s native gesture navigation with any 3rd party launcher
Google has introduced native gesture-based navigation in Android 10. But as you probably have noticed, it doesn’t work with 3rd party launchers. Well, there is a simple ADB command that can activate A10 gestures on any 3rd party launcher (I use Nova Prime). The command is:
A better approach would be to ditch Android 10’s half-baked gestures completely and using a better app like Fluid NG/ Edge Gestures. I don’t like using an extra app just for this purpose, so I’m sticking with the ADB method.
5. Change the height of the navigation bar
Android’s default nav bar takes up too much space on your screen. You can adjust its height with a simple command. Fortunately, it is not affected by reboot. The command is:
I’m using –59, but you can tune it to your liking. A positive value would push the navigation bar up, while negative value would push it down (partially/fully hiding it even, of course).
To reset the original height of the navigation bar:
6. Add Left/Right Keyboard Cursors to the Nav Bar during Text Input
This super handy tweak adds left/right keyboard cursors to the nav bar while the keyboard is showing, making it super easy to edit typos/scroll through words quickly. This article on XDA describes it in detail.
Greenify is one of the few apps that can actually improve your device’s battery life. To utilize this amazing app to its full potential, you’re going to need root access and Xposed framework. But most of its features can be activated using ADB. And it’s all a one-time process, so that’s very convenient. You should disable battery optimization for Greenify & enable notification access, accessibility service & device admin option for Greenify to get the best results. These are the adb commands to activate Greenify without root: [Source: This article]
Note: [On some Chinese devices (MIUI, ColorOS etc), you need to enable «USB debugging (Security settings)» from developer settings before executing the adb commands given below. The source article didn’t mention this]
Now force stop Greenify to let the granted permission take effect and then turn on the accessibility service manually. You can force stop the app using the following command:
Here is a list of apps I’ve greenified: Click this link too see the SS gallery
Naptime by Francisco Franco is another great app which works with ADB but I think Greenify alone is enough, for me at least.
8. App: Quick Settings
This app is tiny but extremely powerful. It allows you to add some really useful buttons to your quick settings panel. You can activate immersive mode, so you can hide status bar / navigation bar (or both) with a single click; useful if you want to use a dedicated gesture navigation app.
I have enabled screenshot button, reverse portrait, screen off toggle, caffeine, power button, volume control and a bunch of other super useful toggles using this app. To use Quick Settings app without root access, just connect your device to ADB and type (one-time process):
And yes, make sure to follow the in-app YouTube video to learn how to activate the quick settings tiles and disable battery optimization for this app & turn the accessibility service on.
9. Stop Vibrations from Any Android App on Your Phone:
This one is taken from THIS xda article.
Some apps & malicious ads on the web tend to abuse the vibration permission. Don’t you find it kinda funny when a random ad pops up (with intense vibrations ) telling you Microsoft technical support needs to be contacted immediately to remove the Windows virus from your Android device You can disable vibration with this simple tweak
10. Advanced app permission management with Shizuku & App Ops
Android has a native app permission management system. By default, there is no user accessible way of manipulating it without root access. That’s where these two apps come in handy. Shizuku is the framework & App Ops is the app that we can use to manipulate app permissions. First of all, download the apps:
First of all, go to:
— Settings → Apps & notification → SEE ALL APPS → Shizuku
Click on ‘Permissions’ and you’ll see ‘Additional permissions’. Click on it, and allow it the permission called ‘Shizuku’
— Now repeat the previous steps for the 2nd app, App Ops
At this point, you have to start Shizuku server via ADB. Open a command prompt and enter the following command:
Note: You have to execute this command every time you reboot your device
Open Shizuku and the app should say “Shizuku is running Version 8, adb” & “Authorized 1 application” – that means Shizuku has been configured correctly; see the SS:
Now launch App Ops, choose ADB mode (the first option), finish the intro and you’re good to go. You’ll see a list of your apps. You can view an app’s permissions by clicking on it & enable / disable them.
Note: This step is not mandatory; but if Shizuku keeps closing in the background, you should read the paragraph called «5. Shizuku randomly stops?» on this page.
This application makes it very easy to mirror you phone’s screen to your PC/laptop’s monitor. It’s a very useful tool in my opinion. Once you use this program, you will find new reasons to keep using it It even supports copy-pasting from your PC to android & vice versa. And it works over Wi-Fi too.
From the project’s GitHub readme:
60fps)
— quality (1920×1080 or above)
— low latency (35
70ms)
— low startup time (
1 second to display the first image)
— non-intrusiveness (nothing is left installed on the device)
Download: CLICK HERE to check & download the latest version OR, CLICK HERE to download v1.14 directly
How to use: Using this application is very easy. This program comes with adb binary, so just extract the zip file in a convenient location, connect your phone to your PC, and open a command prompt in that folder & type:
You should see a window with your device’s screen. It’s that simple.
Okay, this application has a ton of options & keyboard shortcuts. Follow the project’s GitHub page to learn more. I’m just listing the most useful controls here:
— Left mouse click = selects items
— Middle Mouse click (clicking the scroll wheel) = sends the current app to background
— The scroll wheel scrolls thru content
— You can write using your PC’s keyboard
— Right mouse click = back button
— Ctrl+r = Rotates the screen
— Ctrl+p acts like power button. Pressing this combo once will lock your device & pressing it again will wake the device up and bring up the lock screen. You can unlock the device without touching it; just draw the pattern with your mouse / type in the PIN.
— By default, scrcpy keeps you device’s screen on. I find that annoying. Thankfully, the dev has thought of it. Pressing Ctrl+o will turn off the display, but Scrcpy will keep mirroring the screen.
You can also limit the frame rate, reduce the resolution and bit rate to improve mirroring performance. I’d suggest reducing the bit rate first if your device’s output seems laggy. It’s also possible to record the screen while mirroring. I won’t discuss these here; follow the project’s README.md on GitHub to learn more.
As mentioned earlier, this post is a work-in-progress. I’m trying new adb tweaks & I’ll update this post as I find more working ones for Mi A3. If you have some useful ADB tweaks, please share them with us. Thanks and have a nice day