anonymousfox co что это
Someone got into my account and changed my admin Username to AnonymousFox
Please help me change my username. Someone got into my account and changed my admin username. I don’t know how they got it. I’ve read that AnonymousFox has bypassed wordpress security. Please help me to know what parts of my files to protect.
What is the URL of the site you are trying to access? We’ll be happy to take a look and see if we can help.
Your site is not hosted with WordPress.com. It is a site using the open-source WordPress software (from WordPress.org) but hosted elsewhere.
Because WordPress.com and WordPress.org are two entirely separate entities, we cannot access files or data for sites that are hosted elsewhere, so WordPress.com staff can only assist with sites that are hosted on our servers. You can find more information here about the differences between WordPress.org software and WordPress.com: https://wordpress.com/support/com-vs-org/
https://wordpress.org/support/ is a great resource for sites using the open source WordPress.org software, and you can find support for that at: https://wordpress.org/support/forums/
Your hosting provider’s support team may also be able to assist.
Thanks for your reply. It has been confusing on the forums to find real answers.
I’ve reached out to my hosting provider.
Just make sure you’ve got backups first, and know how to restore one if needed.
The topic ‘Someone got into my account and changed my admin Username to AnonymousFox’ is closed to new replies.
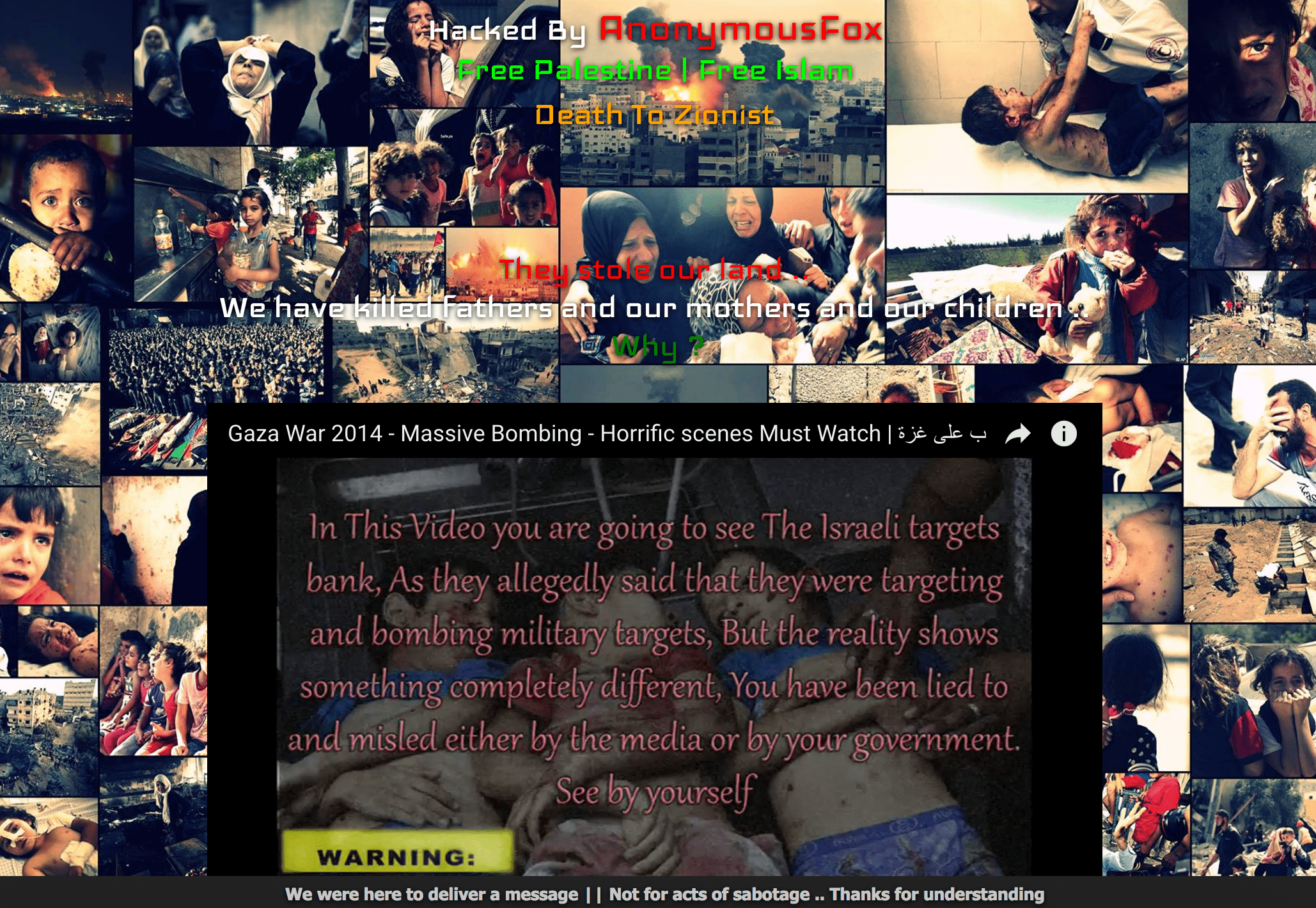
82 Kazakhstan Websites Hacked by AnonymousFox
A hacker going by the alias of AnonymousFox has hacked 82 Kazakhstan Websites, including 7 high profiled Kazakhstan governmental agencies. The attack seems to be a mass defacement of the server. The motive of the attack stated by the hacker himself on the deface page’s footer was:
The hacker also displays a Pro-Palestinian and Anti-Zionist message. The exact quotes being:
The hacker seems to be on a mission to spread the message of the illegal occupation and the killing of innocent civilians of the Palestinian people by the Israeli Defence Forces. The attacker attaches a graphic video of the violence upon the Palestinian people by the Israeli Defence Force in the 2014 Gaza War. The video can be disturbing to some viewers so watch at your own discretion.
The defacements of all 82 websites have been recovered as of the writing of this article. However, the attack has been mirrored onto Zone-H Cached Archives with all the list of websites that have fallen victim to the attack.
The Kazakhstan government agencies or the server sysadmins are yet to provide a public statement on the breach and the point of vulnerability that lead to the mass defacement of their servers.
The never ending war between Israel and Palestine has made its way from the streets through to the Internet. Hackers, especially those believing in the Islamic religion, tend to show their political views in regard to the Israeli-Palestinian conflict by posting it onto as many websites as they can in the form of defacements to somewhat raise awareness. Regardless of the fact that it may seem an act of hacktivism from the eyes of the hackers, the attacks can cause cost damages, and a waste in time.
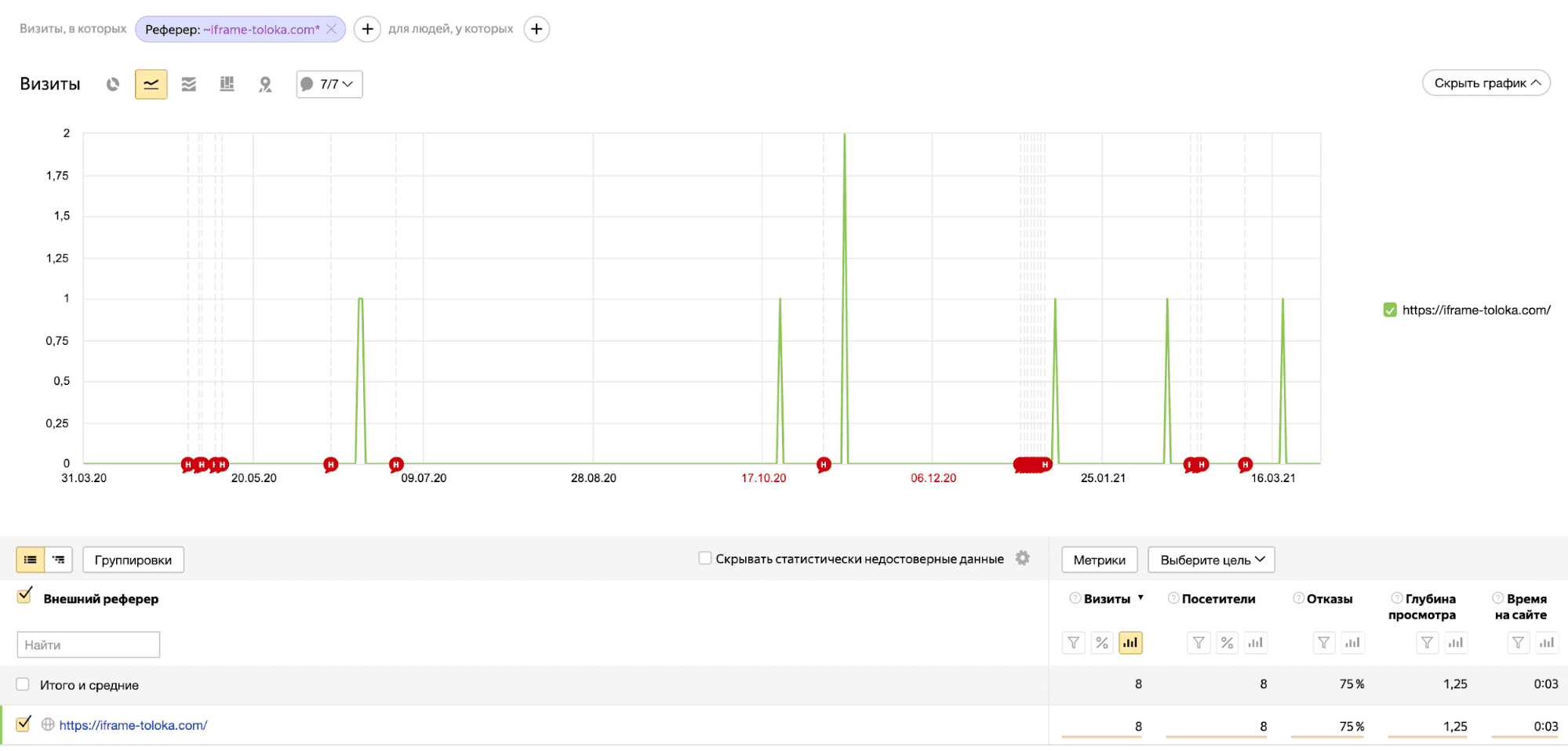
Переходы с iframe-toloka.com — что это значит?
Часто владельцы «молодых» сайтов наблюдают следующую картину: переходы на сайт с iframe-toloka.com. Что это значит? Разберемся в нашей статье. Переходы с iframe-toloka.com свидетельствуют о том, что ваш сайт посетили асессоры Яндекса. Скорее всего, они оценили его качество, юзабилити, релевантность поисковому запросу. Нужно ли из-за этого паниковать? Ни в коем случае. Ниже мы подробно разберем, как асессоры влияют на продвижение сайта.
Кто такие асессоры
Асессоры — это специальные люди, которые помогают поисковым алгоритмам обучаться и вручную указывают на то, какие страницы следует считать релевантными по запросу.
Существует специальный сервис «Яндекс Толока». Зарегистрироваться в нем может практически любой желающий. В этом сервисе люди получают небольшие задания и помогают Яндексу оценить качество веб-ресурсов за денежные вознаграждения.
Как отследить переходы на сайт с iframe-toloka.com
Чтобы понять, заходили на ваш сайт асессоры или нет, следуйте инструкции.
Как могут повлиять переходы с iframe-toloka
Мы выяснили, что асессоры могут оценить качество и релевантность вашего ресурса. Как их оценки могут повлиять на позиции в поиске?
Если ваш сайт долго загружается, на нем много бесполезного или запрещенного контента, ваши позиции могут значительно ухудшиться. Помните, что асессор — обычный человек. Если ему потребуется много времени, чтобы найти ответ на интересующий его вопрос на вашей странице, то и оценка будет низкой.
Если на вашем сайте удобный интерфейс, приятный дизайн, тексты написаны «для людей», а контент в целом отвечает на запросы пользователей, то беспокоиться не о чем. Асессоры дадут вашему ресурсу хорошую оценку, что положительно повлияет на продвижение в Яндексе.
Нужно ли запрещать переходы с iframe-toloka
Мы не рекомендуем этого делать. Если вы уверены в качестве своего контента — не нужно запрещать асессорам посещать ваш ресурс. Если не уверены — работайте над качеством страниц и сайта в целом. Как это делать?
Как анализировать поведение асессоров
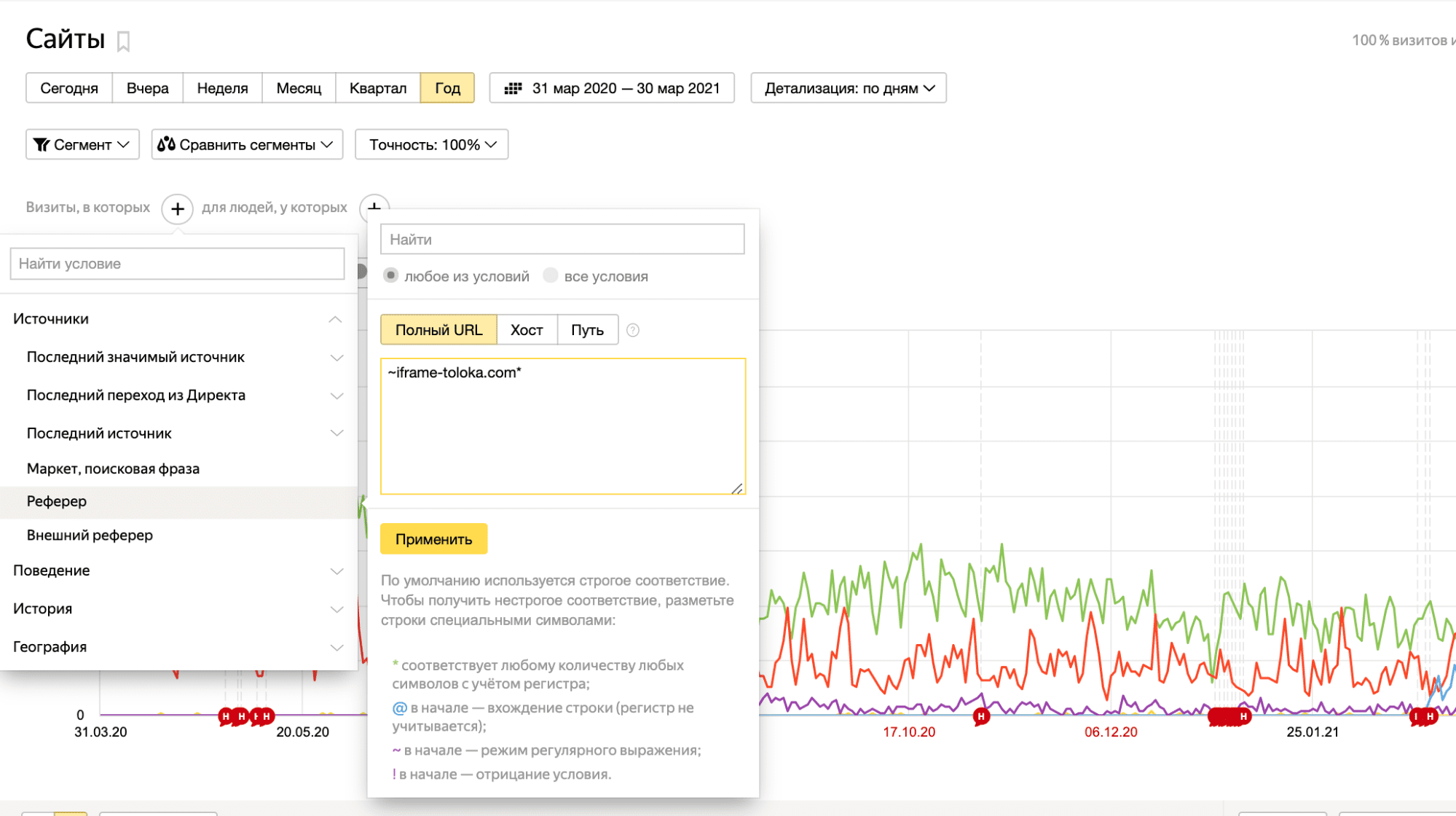
В этом нам снова поможет Яндекс.Метрика. Зайдите в раздел «Вебвизор» и установите фильтр «Источники» > «Реферер» > «
WordPress.org
Support » Fixing WordPress » AnonymousFox_hux wordpress hacked
AnonymousFox_hux wordpress hacked
I have a server with lots of wordpress websites.
I have discovered today a couple of accounts hacked and when digging deeper, have found the user_login field for the admin user in wp_users has been changed to AnonymousFox_hux on most WP databases.
Most databases have a different wp_ prefix so I am assuming that it must be some type of WP vulnerability to mass change the same field ONLY in the WP DB and in the user table (regardless of prefix)
Anyone experienced this and know a potential vulnerability?
Carefully follow this guide. When you’re done, you may want to implement some (if not all) of the recommended security measures and start backing up your site.
@macmanx cleaning the hack is not a problem – I know how to do that and have done it numerous times before.
The hack has occurred on dozens of sites – sites with Wordfence installed – therefore, this issue is bigger than just “my site was hacked”
There is a major hole somewhere (they got through wordfence) and I want to try and identify the hole
This appears to be a wordpress specific vulnerability.
I have had tech support look into the server and can find no trace of any illegal access
All wordpress sites on server have had the user_login field with in the wp_users table updated to – AnonymousFox_hux and the password changed.
One site in particular that got attacked:
1. It had Wordfence installed and running
2. All WP software and plugins were up to date
NOTE: I have run a full scan with wordfence and no damage or malware found on this updated, protected site.
This appears to be a wordpress specific vulnerability.
Support
Admin Tools
#31631 – Super User: name & password have been changed
Dear Akeeba-Team, Nicholas,
we experienced the weirdest issue:
1. Did you experience/heard of something similar before? Couldn’t find any info on this online, the only thing that pops up and it is similar is about an «AnonymousFox» hack, but that was WordPress-only.
2. Shouldn’t AdminTools have prevented this by default?
3. Is there any way to check in the Joomla backend for when updates were made, and from what version? Some kind of a update log? For Joomla itself, but also 3rd party extensions as AdminTools?
All best, με εκτίμηση,
Custom Fields
| Joomla! version (in x.y.z format) | 3.9.x |
| PHP version (in x.y.z format) | 7.1.31 |
| Admin Tools version (x.y.z format) | 5.3.x |
1. I have not heard of that before. I can speculate about what happened but I’d rather not until we resolve point #2.
2. It depends. Have you enabled the «Disable editing backend users’ properties», «Disable creating / editing backend users from the frontend» and «Monitor Super User accounts» features in Hardening Options in the Configure WAF page? The first one prevents using the Joomla backend Users page or the Joomla API to create or modify any user with backend access privileges from the backend and frontend. The second option prevents using the Joomla API to create or modify any user with backend access privileges from the frontend of the site. The latter option is an added safety feature which immediately disables any user with backend access which was NOT created through Joomla’s backend Users page.
If you had not enabled all of these and especially the third feature, no, Admin Tools could not have protected you because you told it not to.
Please note that just because your site is not deliberately listed on search engines does not mean that it cannot be found. There are other ways such as trawling whole IP ranges for specific kinds of server, looking for recently registered domain names etc. Not to mention that just because you didn’t manually submit your site to a search engine it doesn’t mean the search engine didn’t pick it up. I am pretty sure that Google Chrome sends back telemetry including the URLs you are visiting.
3. No. You can use the User Actions Log to keep a log of actions initiated by humans logged into the site’s backend. However, this feature cannot tell you about automated / out-of-site actions (e.g. Plesk auto-updating Joomla or myJoomla updating Akeeba Backup for example) and its utility is limited by extensions’ support for it. We have added support in all our software and Joomla core extensions do support it.
In any case I would recommend that you reset all of your passwords (Plesk, FTP, database, Joomla) and that you make sure that both Joomla and Plesk itself are up-to-date. Regarding your passwords, I very strongly recommend using 32 to 64 character (a-z, A-Z, 0-9 and special characters [email protected]#$%^&*()_+-=<>[];:'»\|, /? ) truly randomly generated by and stored in a password manager.
thank you for the quick reply!
On 2:
YES: «Disable editing backend users’ properties»
YES: «Disable creating / editing backend users from the frontend»
NO: «Monitor Super User accounts»
So, if I understood correctly, the attack was not coming from Joomla, it was bypassed?
A server issue?
How can I verify if this happened?
Since the third option was not enabled there was no way for Admin Tools to detect the Super User change coming outside of Joomla’s API. The reason we added this feature was the fact that Super User changes can be applied directly to the database by an attacker exploiting a SQL injection or remote code execution vulnerability.
It can also be that the attacker guessed or stole your login information for either Plesk or FTP. As I mentioned before, just because you don’t have search engines crawl your site or purpose does not mean it’s «hidden». It is on a live server connected to the Internet. There are a myriad different ways finding it. At the very least, it shares an IP address with some of your live, indexed sites. If I were a hacker I’d look for Joomla sites, then do a search on their IP addresses to find other domains on the same IP which are probably going to be similar installations of the same vintage. Passwords can be stolen either by someone sniffing the network for traffic (not too hard on a public Wi-Fi such as hotel, cafeteria or airport) or via malware. Most usually it is guessed because the default account passwords in Plesk, cPanel etc are woefully insecure and only meant to facilitate novices. As I mentioned, change all passwords and use something really, really long and complex.
Regarding detection. I cannot tell you anything more as I’m not you 🙂 Since you have the server logs you could check for any unusual logins or FTP connections. It would also be a good idea checking the web server’s access logs around the time the change occurred.