Ip local pool cisco привязка к машине ip
DHCP по VLAN на коммутаторах Cisco
Немного теории для самых маленьких
VLAN или Virtual Local Area Network — виртуальная локальная компьютерная сеть, представляет собой группу хостов с общим набором требований, которые взаимодействуют так, как если бы они были подключены к широковещательному домену, независимо от их физического местонахождения.
Другими словами VLAN — это технология сегментации локальной сети на более мелкие виртуальные локальные сети со своим широковещательным доменом.
Вступление
О том что такое DHCP я думаю рассказывать не нужно, но для тех кто «не уверен» есть хорошая статья, можно почитать здесь. Также там описаны базовые настройки DHCP на маршрутизаторах Cisco. Они ничем не отличаются и для коммутаторов. Добавлю лишь то, что перед тем как конфигурировать DHCP необходимого включить ip routing на свитче, что бы поднять его на уровень 3 и осуществлять межвлановую маршрутизацию, для чего в свою очередь необходимо в режиме глобальной конфигурации ввести соответствующую команду:
Всем известно, что использовать протокол DHCP очень удобно — так как у администратора сети отпадает необходимость в настройке стека протоколов TCP/IP для каждой клиентской машины. С другой стороны, в общем случае адреса назначаются случайным образом, и заранее неизвестно какой хост получит какой адрес. А если необходимо сохранить какой-то порядок назначения адресов, что делать в таком случае!?
1-ое решение: Сохранив удобство использования DHCP привязать каждый компьютер к определенному IP-адресу, так называемая привязка к MAC-адресу: на DHCP-сервере хранится таблица адресов, где IP привязаны MAC’ам, в соответствии с которой происходит выдача. Таблица заполняется по мере добавления компьютеров в сеть.
Минусы этого решения в том, что администратору необходимо отслеживания MAC-адреса и сопровождать таблицы соответствия на сервере.
Решение №2: Поставить IP-адреса в соответствие не MAC-адресам, а портам коммутатора уровня доступа, к которым подключены клиентские компьютеры.
Решение №3 Выдача IP-адресов происходит в зависимости от того с какого DHCP-ретранслятора пришел запрос. В данном случае адреса выдаются из одной подсети, но с привязкой конкретных диапозонов адресов к конкретным коммутаторам, работающим как DHCP-ретрансляторы (dhcpsnooper). Это может довольно существенно помочь администратору сети, так как по IP-адресу клиентского компьютера сразу понятно к какому коммутаторы он подключен. Для этого решения используется опция 82 протокола DHCP.
Решение №4 (И самое гибкое): Раздавать IP-адреса по VLAN. Так мы получаем некое универсальное решение включающее преимущества всех предыдущих. Гибкость такого решения практически безгранична.
Практическая сторона вопроса
Вот и все, готово! Компьютеры при подключении к сети получат IP-адреса по протоколу DHCP в соответствии с пулами для VLAN’ов в которых они находятся.
В реальных сетях возможно целесообразно разделение VLAN’ами по этажам или по отделам и т.д. как вам будет удобно. Таким образом, раздача IP-адресов теперь полностью в ваших руках.
Cisco Security Appliance Command Line Configuration Guide, Version 7.2
Book Title
Cisco Security Appliance Command Line Configuration Guide, Version 7.2
Chapter Title
Configuring IP Addresses for VPN
View with Adobe Reader on a variety of devices
Results
Chapter: Configuring IP Addresses for VPN
Configuring IP Addresses for VPNs
This chapter describes IP address assignment methods.
IP addresses make internetwork connections possible. They are like telephone numbers: both the sender and receiver must have an assigned number to connect. But with VPNs, there are actually two sets of addresses: the first set connects client and server on the public network. Once that connection is made, the second set connects client and server through the VPN tunnel.
In security appliance address management, we are dealing with the second set of IP addresses: those private IP addresses that connect a client with a resource on the private network, through the tunnel, and let the client function as if it were directly connected to the private network. Furthermore, we are dealing only with the private IP addresses that get assigned to clients. The IP addresses assigned to other resources on your private network are part of your network administration responsibilities, not part of VPN management. Therefore, when we discuss IP addresses here, we mean those IP addresses available in your private network addressing scheme that let the client function as a tunnel endpoint.
This chapter includes the following sections:
•
•
•
•
Configuring an IP Address Assignment Method
The security appliance can use one or more of the following methods for assigning IP addresses to remote access clients. If you configure more than one address assignment method, the security appliance searches each of the options until it finds an IP address. By default, all methods are enabled. To view the current configuration, enter the show running-config all vpn-addr-assign command.
• 
• 
• 
To specify a method for assigning IP addresses to remote access clients, enter the vpn-addr-assign command in global configuration mode. The syntax is vpn-addr-assign
Configuring Local IP Address Pools
To configure IP address pools to use for VPN remote access tunnels, enter the ip local pool command in global configuration mode. To delete address pools, enter the no form of this command.
The security appliance uses address pools based on the tunnel group for the connection. If you configure more than one address pool for a tunnel group, the security appliance uses them in the order in which they are configured.
If you assign addresses from a non-local subnet, we suggest that you add pools that fall on subnet boundaries to make adding routes for these networks easier.
A summary of the configuration of local address pools follows:
Step 1 
Step 2 
The following example configures an IP address pool named firstpool. The starting address is 10.20.30.40 and the ending address is 10.20.30.50. The network mask is 255.255.255.0.
Configuring AAA Addressing
In addition, the user must match a tunnel group configured for RADIUS authentication.
The following examples illustrate how to define a AAA server group called RAD2 for the tunnel group named firstgroup. It includes one more step than is necessary, in that previously you might have named the tunnel group and defined the tunnel group type. This step appears in the following example as a reminder that you have no access to subsequent tunnel-group commands until you set these values.
An overview of the configuration that these examples create follows:
To configure AAA for IP addressing, perform the following steps:
Step 1 
Step 2 
Step 3 
Step 4 
This command has more arguments that this example includes. For more information, see the Cisco Security Appliance Command Reference.
Configuring DHCP Addressing
To use DHCP to assign addresses for VPN clients, you must first configure a DHCP server and the range of IP addresses that the DHCP server can use. Then you define the DHCP server on a tunnel group basis. Optionally, you can also define a DHCP network scope in the group policy associated with the tunnel group or username. This is either an IP network number or IP Address that identifies to the DHCP server which pool of IP addresses to use.
The following examples define the DHCP server at IP address 172.33.44.19 for the tunnel group named firstgroup. They also define a DHCP network scope of 192.86.0.0 for the group policy called remotegroup. (The group policy called remotegroup is associated with the tunnel group called firstgroup). If you do not define a network scope, the DHCP server assigns IP addresses in the order of the address pools configured. It goes through the pools until it identifies an unassigned address.
The following configuration includes more steps than are necessary, in that previously you might have named and defined the tunnel group type as remote access, and named and identified the group policy as internal or external. These steps appear in the following examples as a reminder that you have no access to subsequent tunnel-group and group-policy commands until you set these values.
A summary of the configuration that these examples create follows:
To define a DHCP server for IP addressing, perform the following steps.
Step 1 
Step 2 
Step 3 
Step 4 
Step 5 
Step 6 
Step 7 
Step 8 
CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.1
Book Title
CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.1
Chapter Title
Configuring IP Addresses for VPN
View with Adobe Reader on a variety of devices
Results
Chapter: Configuring IP Addresses for VPN
Configuring IP Addresses for VPNs
This chapter describes IP address assignment methods.
IP addresses make internetwork connections possible. They are like telephone numbers: both the sender and receiver must have an assigned number to connect. But with VPNs, there are actually two sets of addresses: the first set connects client and server on the public network. Once that connection is made, the second set connects client and server through the VPN tunnel.
In ASA address management, we are dealing with the second set of IP addresses: those private IP addresses that connect a client with a resource on the private network, through the tunnel, and let the client function as if it were directly connected to the private network. Furthermore, we are dealing only with the private IP addresses that get assigned to clients. The IP addresses assigned to other resources on your private network are part of your network administration responsibilities, not part of VPN management. Therefore, when we discuss IP addresses here, we mean those IP addresses available in your private network addressing scheme that let the client function as a tunnel endpoint.
This chapter includes the following sections:
Configuring an IP Address Assignment Policy
The ASA can use one or more of the following methods for assigning IP addresses to remote access clients. If you configure more than one address assignment method, the ASA searches each of the options until it finds an IP address. By default, all methods are enabled.
– Allow the reuse of an IP address so many minutes after it is released—Delays the reuse of an IP address after its return to the address pool. Adding a delay helps to prevent problems firewalls can experience when an IP address is reassigned quickly. By default the ASA does not impose a delay. This configurable element is available for IPv4 assignment policies.
Use one of these methods to specify a way to assign IP addresses to remote access clients.
Configuring IPv4 Address Assignments at the Command Line
ciscoasa(config)# vpn-addr-assign aaa
ciscoasa(config)# vpn-addr-assign local reuse-delay 180
ciscoasa(config)# no vpn-addr-assign dhcp
Enables an address assignment method for the ASA to use when assigning IPv4 address to VPN connections. The available methods to obtain an IP address are from a AAA server, DHCP server, or a local address pool. All of these methods are enabled by default.
For local IP address pools, you can configure the reuse of an IP address for between 0 and 480 minutes after the IP address has been released.
Use the no form of the command to disable an address assignment method.
Configuring IPv6 Address Assignments at the Command Line
ciscoasa(config)# ipv6-vpn-addr-assign aaa
ciscoasa(config)# no ipv6-vpn-addr-assign local
Enables an address assignment method for the ASA to use when assigning IPv6 address to VPN connections. The available methods to obtain an IP address are from a AAA server or a local address pool. Both of these methods are enabled by default.
Use the no form of the command to disable an address assignment method.
The following table shows the modes in which this feature is available:
Viewing Address Assignment Methods
Use one of these methods to view the address assignment method configured on the ASA:
Viewing IPv4 Address Assignments from the Command Line
show running-config all vpn-addr-assign
ciscoasa(config)# show running-config all vpn-addr-assign
Shows the configured address assignment method. Configured address methods could be aaa, dhcp, or local.
Viewing IPv6 Address Assignments from the Command Line
show running-config all ipv6-vpn-addr-assign
hostname(config)# show running-config all ipv6-vpn-addr-assign
Shows the configured address assignment method. Configured address methods could be aaa or local.
ipv6-vpn-addr-assign local reuse-delay 0
Configuring Local IP Address Pools
To configure IPv4 address pools to use for VPN remote access tunnels, enter the ip local pool command in global configuration mode. To delete address pools, enter the no form of this command.
To configure IPv6 address pools to use for VPN remote access tunnels, enter the ipv6 local pool command in global configuration mode. To delete address pools, enter the no form of this command.
The ASA uses address pools based on the connection profile or group policy for the connection. The order in which you specify the pools is important. If you configure more than one address pool for a connection profile or group policy, the ASA uses them in the order in which you added them to the ASA.
If you assign addresses from a non-local subnet, we suggest that you add pools that fall on subnet boundaries to make adding routes for these networks easier.
Use one of these methods to configure a local IP address pool:
Configuring Local IPv4 Address Pools Using CLI
Configures IP address pools as the address assignment method, enter the vpn-addr-assign command with the local argument. See also Configuring IPv4 Address Assignments at the Command Line.
ip local pool poolname first_address—last_address mask mask
ciscoasa(config)# ip local pool firstpool 10.20.30.40-10.20.30.50 mask 255.255.255.0
ciscoasa(config)# no ip local pool firstpool
Configures an address pool. The command names the pool, specifies a range of IPv4 addresses and the subnet mask.
Configuring Local IPv6 Address Pools Using CLI
Configures IP address pools as the address assignment method, enter the ipv6- vpn-addr-assign command with the local argument. See also Configuring IPv6 Address Assignments at the Command Line.
ipv6 local pool pool_name starting_address prefix_length number_of_addresses
ciscoasa(config)# ipv6 local pool ipv6pool 2001:DB8::1/32 100
ciscoasa(config)# no ipv6 local pool ipv6pool
Configures an address pool. The command names the pool, identifies the starting IPv6 address, the prefix length in bits, and the number of addresses to use in the range.
Assign Internal Address Pools to Group Policies in ASDM
The Add or Edit Group Policy dialog box lets you specify address pools, tunneling protocols, filters, connection settings, and servers for the internal Network (Client) Access group policy being added or modified. For each of the fields on this dialog box, checking the Inherit check box lets the corresponding setting take its value from the default group policy. Inherit is the default value for all the attributes in this dialog box.
You can configure both IPv4 and IPv6 address pools for the same group policy. If both versions of IP addresses are configured in the same group policy, clients configured for IPv4 will get an IPv4 address, clients configured for IPv6 will get an IPv6 address, and clients configured for both IPv4 and IPv6 addresses will get both an IPv4 and an IPv6 address.
Step 1 Connect to the ASA using ASDM and select Configuration > Remote Access VPN > Network (Client) Access > Group Policies.
Step 2 Create a new group policy or the group policy you want to configure with an internal address pool and click Edit.
The General attributes pane is selected by default in the group policy dialog.
Step 3 Use the Address Pools field to specify an IPv4 address pool for this group policy. Click Select to add or edit an IPv4 address pool.
Step 4 Use the IPv6 Address Pools field to specify an IPv6 address pools to use for this group policy. Click Select to add or edit a IPv6 address pool.
Step 6 Click Apply.
Configuring AAA Addressing
To use a AAA server to assign addresses for VPN remote access clients, you must first configure a AAA server or server group. See the aaa-server protocol command in the command reference.
In addition, the user must match a connection profile configured for RADIUS authentication.
The following examples illustrate how to define a AAA server group called RAD2 for the tunnel group named firstgroup. It includes one more step than is necessary, in that previously you might have named the tunnel group and defined the tunnel group type. This step appears in the following example as a reminder that you have no access to subsequent tunnel-group commands until you set these values.
An overview of the configuration that these examples create follows:
To configure AAA for IP addressing, perform the following steps:
Step 1 To configure AAA as the address assignment method, enter the vpn-addr-assign command with the aaa argument:
Step 2 To establish the tunnel group called firstgroup as a remote access or LAN-to-LAN tunnel group, enter the tunnel-group command with the type keyword. The following example configures a remote access tunnel group.
Step 3 To enter general-attributes configuration mode, which lets you define a AAA server group for the tunnel group called firstgroup, enter the tunnel-group command with the general-attributes argument.
Step 4 To specify the AAA server group to use for authentication, enter the authentication-server-group command.
This command has more arguments that this example includes. For more information, see the command reference.
Configuring DHCP Addressing
To use DHCP to assign addresses for VPN clients, you must first configure a DHCP server and the range of IP addresses that the DHCP server can use. Then you define the DHCP server on a connection profile basis. Optionally, you can also define a DHCP network scope in the group policy associated with a connection profile or username. This is either an IP network number or IP Address that identifies to the DHCP server which pool of IP addresses to use.
The following configuration includes more steps than are necessary, in that previously you might have named and defined the connection profile type as remote access, and named and identified the group policy as internal or external. These steps appear in the following examples as a reminder that you have no access to subsequent tunnel-group and group-policy commands until you set these values.
Guidelines and Limitations
You can only use an IPv4 address to identify a DHCP server to assign client addresses.
Configuring DHCP Addressing Using the CLI
Configures IP address pools as the address assignment method. Enter the vpn-addr-assign command with the dhcp argument. See also Configuring IPv4 Address Assignments at the Command Line.
tunnel-group firstgroup type remote-access
Establishes the connection profile called firstgroup as a remote access connection profile.
Enter the tunnel-group command with the type keyword and remote-access argument.
tunnel-group firstgroup general-attributes
Enters the general-attributes configuration mode for the connection profile so that you can configure a DHCP server.
Enter the tunnel-group command with the general-attributes argument.
Defines the DHCP server by IPv4 address. You can not define a DHCP server by an IPv6 address. You can specify more than one DHCP server address for a connection profile.
Enter the dhcp-server command. This command will allow you to configure the ASA to send additional options to the specified DHCP servers when it is trying to get IP addresses for VPN clients. See the dhcp-server command in the Cisco Security Appliance Command Reference guide for more information.
The example configures a DHCP server at IP address 172.33.44.19.
Exit tunnel-group mode.
Enter the group-policy command with the internal argument to make an internal group policy.
The example configures an internal group.
(Optional) Enters group-policy attributes configuration mode, which lets you configure a subnetwork of IP addresses for the DHCP server to use.
Enter the group-policy command with the attributes keyword.
The example enters group policy attributes configuration mode for remotegroup group-policy.
The example configures a network scope of 192.86.0.0.
Note The dhcp-network-scope must be a routable IP address and not the subset of the DHCP pool. The DHCP server determines which subnet this IP address belongs to and assigns an IP address from that pool. Cisco recommends that you use an interface of the ASA as a dhcp-network-scope for routing reasons. You can use any IP address as the dhcp-network-scope, but it may require that static routes be added to the network.
Example
A summary of the configuration that these examples create follows:
Assigning IP Addresses to Local Users
Local user accounts can be configured to use a group policy, and some AnyConnect attributes can also be configured. These user accounts provide fallback if the other sources of IP address fail, so administrators will still have access.
This section describes how to configure all the attributes of a local user.
Prerequisites
User Edits
By default, the Inherit check box is checked for each setting on the Edit User Account screen, which means that the user account inherits the value of that setting from the default group policy, DfltGrpPolicy.
To override each setting, uncheck the Inherit check box, and enter a new value. The detailed steps that follow describe each of the settings on the Edit User Account screen.
Detailed Steps
The Edit User Account screen opens.
Step 4 Specify a group policy for the user. The user policy will inherit the attributes of this group policy. If there are other fields on this screen that are set to Inherit the configuration from the Default Group Policy, the attributes specified in this group policy will take precedence over those in the Default Group Policy.
Step 5 Specify which tunneling protocols are available for the user, or whether the value is inherited from the group policy. Check the desired Tunneling Protocols check boxes to choose the VPN tunneling protocols that are available for use. Only the selected protocols are available for use. The choices are as follows:
Note If no protocol is selected, an error message appears.
Step 6 Specify which filter (IPv4 or IPv6) to use, or whether to inherit the value from the group policy. Filters consist of rules that determine whether to allow or reject tunneled data packets coming through the ASA, based on criteria such as source address, destination address, and protocol. To configure filters and rules, choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit > General > More Options > Filter.
Click Manage to display the ACL Manager pane, on which you can add, edit, and delete ACLs and ACEs.
Step 7 Specify whether to inherit the Connection Profile (tunnel group) lock or to use the selected tunnel group lock, if any. Selecting a specific lock restricts users to remote access through this group only. Tunnel Group Lock restricts users by checking if the group configured in the VPN client is the same as the users assigned group. If it is not, the ASA prevents the user from connecting. If the Inherit check box is not checked, the default value is None.
Step 8 Specify whether to inherit the Store Password on Client System setting from the group. Uncheck the Inherit check box to activate the Yes and No radio buttons. Click Yes to store the logon password on the client system (potentially a less-secure option). Click No (the default) to require the user to enter the password with each connection. For maximum security, we recommend that you not allow password storage.
Step 9 Specify an Access Hours policy to apply to this user, create a new access hours policy for the user, or leave the Inherit box checked. The default value is Inherit, or, if the Inherit check box is not checked, the default value is Unrestricted.
Click Manage to open the Add Time Range dialog box, in which you can specify a new set of access hours.
Step 10 Specify the number of simultaneous logons by the user. The Simultaneous logons parameter specifies the maximum number of simultaneous logons allowed for this user. The default value is 3. The minimum value is 0, which disables logon and prevents user access.
Note While there is no maximum limit, allowing several simultaneous connections could compromise security and affect performance.
Step 11 Specify the maximum connection time for the user connection time in minutes. At the end of this time, the system terminates the connection. The minimum is 1 minute, and the maximum is 2147483647 minutes (over 4000 years). To allow unlimited connection time, check the Unlimited check box (the default).
Step 12 Specify the Idle Timeout for the user in minutes. If there is no communication activity on the connection by this user in this period, the system terminates the connection. The minimum time is 1 minute, and the maximum time is 10080 minutes. This value does not apply to users of clientless SSL VPN connections.
Step 13 Configure the Session Alert Interval. If you uncheck the Inherit check box, the Default checkbox is checked automatically. This sets the session alert interval to 30 minutes. If you want to specify a new value, uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the minutes box.
Step 14 Configure the Idle Alert Interval. If you uncheck the Inherit check box, the Default checkbox is checked automatically. This sets the idle alert interval to 30 minutes. If you want to specify a new value, uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the minutes box.
Step 15 To set a dedicated IPv4 address for this user, enter an IPv4 address and subnet mask in the Dedicated IPv4 Address (Optional) area.
Step 16 To set a dedicated IPv6 address for this user, enter an IPv6 address with an IPv6 prefix in the Dedicated IPv6 Address (Optional) field. The IPv6 prefix indicates the subnet on which the IPv6 address resides.
The changes are saved to the running configuration.
Cisco Remote Access IPsec VPN (EzVPN)
Меня всегда интересовало, что же такого легкого в EzVPN, что позволяет Cisco называть его так 🙂 Настройка сервера может быть весьма и весьма развесистой, однако кардинальных отличий от Site-to-Site не так уж и много и заключаются они в так называемой ISAKMP/IKE Phase 1.5, а конкретно в механизме XAUTH.
Cisco Easy VPN оперирует двумя понятиями – Cisco Easy VPN сервер и Cisco Easy VPN Remote (удаленный агент). В качестве агента могут выступать некоторые маршрутизаторы, ASA МСЭ, компьютеры с установленным Cisco VPN Client. OS X и iPhone/iPad имеют встроенные IPSec клиенты поддерживающие XAUTH (racoon).
Я не буду останавливаться на настройке Cisco Systems Easy VPN Client, однако покажу, как можно настроить маршрутизатор в качестве этого самого клиента (что само по себе не очень актуально из-за разнообразия других технологий, обеспечивающих связность удаленных площадок, но может быть полезно для понимания механизмов взаимодействия).
Настройка Site-to-Site не сильно отличается от Remote Access. Похожие моменты это – политики первой фазы ISAKMP/IKE, transform sets, dynamic & static crypto maps. На этих вещах я подробно останавливаться не буду, если есть желание, то перечитайте статью о site-to-site VPN’ах. И так, приступим, начав с настройки Easy VPN Server.
Определимся с AAA
AAA (Authentication, Authorization, Accounting) используется Easy VPN для применения групповых политик и авторизации, а так же для аутентификации пользователей (XAUTH). Easy VPN сервер может получать информацию о пользователях и группах либо из локальной базы, либо с radius-сервера. Смысл в последнем появляется, когда у вас большая база пользователей и пара-другая точек входа. Настройка AAA сводится к следующему:
Команда aaa new-model включает AAA на маршрутизаторе.
aaa authentication login позволяет пользователям проходить XAUTH аутентификацию (так называемая фаза 1.5) на маршрутизаторе. authentication_list будет использоваться далее как один из параметров crypto map или ISAKMP профиля. В методах можно использовать локальную базу пользователей (в этом случае база заполняется с помощью команды username …) и/или radius сервер. Можно указать несколько методов аутентификации, которые маршрутизатор будет использовать в порядке указанном вами.
aaa authorization network указывает AAA сервер, который будет использоваться для обработки политик IPSec remote access групп. Так же можно указать local базу, radius базу или обе.
Создание групп
Если вы выбрали метод авторизации local для aaa authorization network, то совсем не лишним будет создать группы на маршрутизаторе. Делается это так:
Объяснение очевидных настроек опущено.
ip local pool – создает пул адресов, которые будут назначены пользователям remote access VPN.
crypto isakmp client configuration address-pool local VPN_POOL – позволяет вам связать адресный пул, созданный с помощью команды ip local pool. Если в дальнейшем при конфигурации remote access группы вы не укажите пул адресов, то будет использоваться пул, указанный с помощью этой команды. Так же эта команда позволяет нескольким группам использовать один и тот же пул.
crypto isamkp client configuration group – непосредственно создает группу, которая будет использоваться в процессе авторизации.
key – pre-shared ключ, который будет использоваться в процессе авторизации.
pool – указывает пул из которого будут выделяться ip для подключения Remote Access клиентов.
split-dns – при включении этой опции DNS запросы к домену будут направлены на внутренние DNS сервера, все остальные запросы будут обслуживаться DNS серверами провайдера.
include-local-lan – клиент получает доступ к сетям, присутствующим в его локальной таблице маршрутизации без включения опции split-tunnel.
netmask – назначает клиенту маску подсети для виртуального адаптера.
acl – опция, иначе называемая split-tunnel. Клиенту сообщается список сетей, до которых нужно шифровать трафик. Весь остальной трафик будет отправляться в не шифрованном виде по общим сетям передачи данных. Обратите внимание на то, что настраивается этот split-tunnel ACL с точки зрения маршрутизатора. К примеру, мы хотим чтобы клиенты отправляли трафик только до сети 192.168.1.0/24, которая находится за нашим маршрутизатором-EasyVPN сервером, по зашифрованному каналу:
backup-gateway – сообщает клиенту резервный Easy VPN сервер. Можно указать до 10 серверов.
save-password – позволяет клиенту сохранять пароль, который указывается в процессе аутентификации (XAUTH).
pfs – опция, указывающая на то, что для каждого обмена второй фазы будет использована новая пара ключей, созданных по алгоритму DH
access-restrict – указывает на интерфейсы, которые могут использовать пользователи указанной группа для терминирования защищенных каналов.
group-lock – опция, заставляющая клиента вводить не только имя пользователя и пароль, но и имя группы с pre-shared ключом.
Dynamic & Static Crypto maps
Последнее что осталось – это связать все настройки в крипто карты и применить их на нужном интерфейсе.
Dynamic crypto map
Команда reverse-route, напомню, отвечает за функционал RRI (reverse route injection). При ее подаче в режиме конфигурации динамической крипто карты внутренний адрес клиента (client mode) или частный адрес сети (network extension mode) появляется как статический маршрут в таблице маршрутизации Easy VPN сервера.
Static crypto map и XAUTH
Для начало нам надо связать dynamic crypto map с static crypto map:
Если вы планируете использоваться и dynamic и static crypto map, то назначайте динамическим картам номера выше, чем статическим. Одновременную работу S2S & remote access VPN (функционал ISAKMP профилей) мы рассмотрим в следующей статье.
Затем нам надо указать группу, которая будет использоваться для авторизации в данной крипто карте:
Укажем маршрутизатору, где искать данные, для аутентификации пользователей:
Дальше решается, кто должен инициировать применение политик IKE Mode Config – сервер (ключ initiate) или клиент (ключ respond):
Программные и аппаратные Cisco Easy VPN клиенты сами инициируют IKE Mode Config. Ключ initiate видимо остался для совместимости с какими-то старыми реализациями протокола.
Альтернативно можно указать время, которое отводится пользователю для прохождения аутентификации командой crypto isakmp xauth timeout seconds. Значение по умолчанию равно 60 секундам.
Мониторинг
show crypto session group – показывает активные группы и количество подключенных клиентов
show crypto session brief – показывает активные группы и пользователей
На этом настройка Cisco Easy VPN Server окончена и после применения static crypto map на интерфейса пользователи cisco easy vpn client должны получить возможность подключаться к вашей сети. Настройку клиента я опущу из-за ее очевидности, а вот на конфигурации аппаратных клиентов мы остановимся подробнее.
Настройка Cisco Easy VPN Remote
В качестве Cisco Easy VPN Client могут выступать не только программные клиенты, но и вполне себе взрослые маршрутизаторы. Настройка их весьма проста по сравнению с сервером и единственное что стоит держать в голове это три режима работы Easy VPN клиента – client mode, network extension mode, network extension plus mode.
Главное ограничение client mode состоит в том, что устройства или пользователи, которые находятся за Cisco Easy VPN Server не могут инициировать подключения к устройствам, которые находятся за Cisco Easy VPN Client. В client mode NAT/PAT настраивается автоматически.
Network extension mode симулирует S2S подключение, позволяя устройствам, находящимся за Cisco Easy VPN Server получать доступ к ресурсам за Cisco Easy VPN Client. В этом случае никакие адреса из внутреннего диапазона не назначаются клиенту. Каждая сеть за клиентом, работающим в network extension mode, должна быть уникальной по понятным причинам.
Network extension plus mode – есть комбинация из client mode и network extension mode. В процессе IKE Mode Config loopback адресу маршрутизатора назначается адрес из пула.
Непосредственно настройка сводится к следующему – указывается DHCP Pool (по желанию):
Создается Easy VPN Client профиль и активируется на интерфейсах:
Если групповой профиль на Easy VPN сервере сконфигурирован без опции save-password, позволяющей клиентам сохранять пароль, то толку от настройки клиента
не будет. Вам будет предложено руками в режиме user или exec mode указать имя пользователя и пароль с помощью команды crypto ipsec client ezvpn xauth.
Мониторинг и выявление неполадок Cisco Easy VPN Client (Remote)
show crypto ipsec client ezvpn – отображает информацию о текущем состоянии активных туннелей включая политики, полученные с сервера в процессе IKE Config Mode.
show ip nat statistics – отображает настройку NAT/PAT клиента работающего в client mode.
debug crypto ipsec client ezvpn – помогает выявлять неполадки в конфигурации Cisco Easy VPN.
clear crypto ipsec client ezvpn – удаляет все активные туннели.
Ну и традиционно сочные конфиги для самых терпеливых:
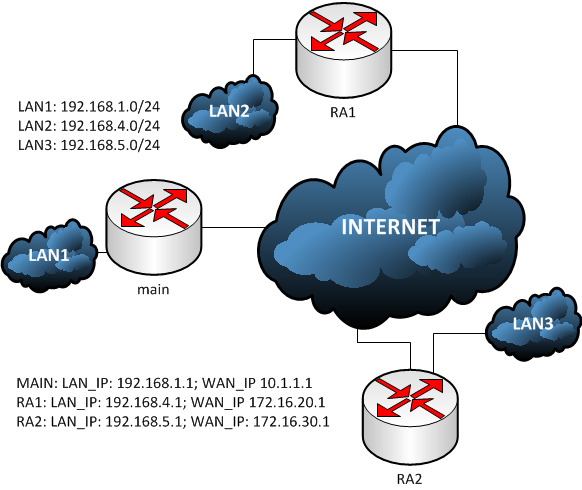
По легенде RA1 работает в client mode и на группу, в которую он входит применен ACL разрешающий ему отправлять трафик, который не предназначен для 192.168.1.0/24 в обход защищенного канала передачи информации. RA2 работает в network extension mode и весь трафик будет отправлен в зашифрованный канал.
main (Cisco Easy VPN Server) configuration:
RA1 (Cisco Easy VPN Client) configuration – client mode:
RA2 (Cisco Easy VPN Client) configuration – network extension mode:
Вот такой вот Easy VPN от Cisco Systems.
CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.1
Book Title
CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.1
Chapter Title
Configuring IP Addresses for VPN
View with Adobe Reader on a variety of devices
Results
Chapter: Configuring IP Addresses for VPN
Configuring IP Addresses for VPNs
This chapter describes IP address assignment methods.
IP addresses make internetwork connections possible. They are like telephone numbers: both the sender and receiver must have an assigned number to connect. But with VPNs, there are actually two sets of addresses: the first set connects client and server on the public network. Once that connection is made, the second set connects client and server through the VPN tunnel.
In ASA address management, we are dealing with the second set of IP addresses: those private IP addresses that connect a client with a resource on the private network, through the tunnel, and let the client function as if it were directly connected to the private network. Furthermore, we are dealing only with the private IP addresses that get assigned to clients. The IP addresses assigned to other resources on your private network are part of your network administration responsibilities, not part of VPN management. Therefore, when we discuss IP addresses here, we mean those IP addresses available in your private network addressing scheme that let the client function as a tunnel endpoint.
This chapter includes the following sections:
Configuring an IP Address Assignment Policy
The ASA can use one or more of the following methods for assigning IP addresses to remote access clients. If you configure more than one address assignment method, the ASA searches each of the options until it finds an IP address. By default, all methods are enabled.
– Allow the reuse of an IP address so many minutes after it is released—Delays the reuse of an IP address after its return to the address pool. Adding a delay helps to prevent problems firewalls can experience when an IP address is reassigned quickly. By default the ASA does not impose a delay. This configurable element is available for IPv4 assignment policies.
Use one of these methods to specify a way to assign IP addresses to remote access clients.
Configuring IPv4 Address Assignments at the Command Line
ciscoasa(config)# vpn-addr-assign aaa
ciscoasa(config)# vpn-addr-assign local reuse-delay 180
ciscoasa(config)# no vpn-addr-assign dhcp
Enables an address assignment method for the ASA to use when assigning IPv4 address to VPN connections. The available methods to obtain an IP address are from a AAA server, DHCP server, or a local address pool. All of these methods are enabled by default.
For local IP address pools, you can configure the reuse of an IP address for between 0 and 480 minutes after the IP address has been released.
Use the no form of the command to disable an address assignment method.
Configuring IPv6 Address Assignments at the Command Line
ciscoasa(config)# ipv6-vpn-addr-assign aaa
ciscoasa(config)# no ipv6-vpn-addr-assign local
Enables an address assignment method for the ASA to use when assigning IPv6 address to VPN connections. The available methods to obtain an IP address are from a AAA server or a local address pool. Both of these methods are enabled by default.
Use the no form of the command to disable an address assignment method.
The following table shows the modes in which this feature is available:
Viewing Address Assignment Methods
Use one of these methods to view the address assignment method configured on the ASA:
Viewing IPv4 Address Assignments from the Command Line
show running-config all vpn-addr-assign
ciscoasa(config)# show running-config all vpn-addr-assign
Shows the configured address assignment method. Configured address methods could be aaa, dhcp, or local.
Viewing IPv6 Address Assignments from the Command Line
show running-config all ipv6-vpn-addr-assign
hostname(config)# show running-config all ipv6-vpn-addr-assign
Shows the configured address assignment method. Configured address methods could be aaa or local.
ipv6-vpn-addr-assign local reuse-delay 0
Configuring Local IP Address Pools
To configure IPv4 address pools to use for VPN remote access tunnels, enter the ip local pool command in global configuration mode. To delete address pools, enter the no form of this command.
To configure IPv6 address pools to use for VPN remote access tunnels, enter the ipv6 local pool command in global configuration mode. To delete address pools, enter the no form of this command.
The ASA uses address pools based on the connection profile or group policy for the connection. The order in which you specify the pools is important. If you configure more than one address pool for a connection profile or group policy, the ASA uses them in the order in which you added them to the ASA.
If you assign addresses from a non-local subnet, we suggest that you add pools that fall on subnet boundaries to make adding routes for these networks easier.
Use one of these methods to configure a local IP address pool:
Configuring Local IPv4 Address Pools Using CLI
Configures IP address pools as the address assignment method, enter the vpn-addr-assign command with the local argument. See also Configuring IPv4 Address Assignments at the Command Line.
ip local pool poolname first_address—last_address mask mask
ciscoasa(config)# ip local pool firstpool 10.20.30.40-10.20.30.50 mask 255.255.255.0
ciscoasa(config)# no ip local pool firstpool
Configures an address pool. The command names the pool, specifies a range of IPv4 addresses and the subnet mask.
Configuring Local IPv6 Address Pools Using CLI
Configures IP address pools as the address assignment method, enter the ipv6- vpn-addr-assign command with the local argument. See also Configuring IPv6 Address Assignments at the Command Line.
ipv6 local pool pool_name starting_address prefix_length number_of_addresses
ciscoasa(config)# ipv6 local pool ipv6pool 2001:DB8::1/32 100
ciscoasa(config)# no ipv6 local pool ipv6pool
Configures an address pool. The command names the pool, identifies the starting IPv6 address, the prefix length in bits, and the number of addresses to use in the range.
Assign Internal Address Pools to Group Policies in ASDM
The Add or Edit Group Policy dialog box lets you specify address pools, tunneling protocols, filters, connection settings, and servers for the internal Network (Client) Access group policy being added or modified. For each of the fields on this dialog box, checking the Inherit check box lets the corresponding setting take its value from the default group policy. Inherit is the default value for all the attributes in this dialog box.
You can configure both IPv4 and IPv6 address pools for the same group policy. If both versions of IP addresses are configured in the same group policy, clients configured for IPv4 will get an IPv4 address, clients configured for IPv6 will get an IPv6 address, and clients configured for both IPv4 and IPv6 addresses will get both an IPv4 and an IPv6 address.
Step 1 Connect to the ASA using ASDM and select Configuration > Remote Access VPN > Network (Client) Access > Group Policies.
Step 2 Create a new group policy or the group policy you want to configure with an internal address pool and click Edit.
The General attributes pane is selected by default in the group policy dialog.
Step 3 Use the Address Pools field to specify an IPv4 address pool for this group policy. Click Select to add or edit an IPv4 address pool.
Step 4 Use the IPv6 Address Pools field to specify an IPv6 address pools to use for this group policy. Click Select to add or edit a IPv6 address pool.
Step 6 Click Apply.
Configuring AAA Addressing
To use a AAA server to assign addresses for VPN remote access clients, you must first configure a AAA server or server group. See the aaa-server protocol command in the command reference.
In addition, the user must match a connection profile configured for RADIUS authentication.
The following examples illustrate how to define a AAA server group called RAD2 for the tunnel group named firstgroup. It includes one more step than is necessary, in that previously you might have named the tunnel group and defined the tunnel group type. This step appears in the following example as a reminder that you have no access to subsequent tunnel-group commands until you set these values.
An overview of the configuration that these examples create follows:
To configure AAA for IP addressing, perform the following steps:
Step 1 To configure AAA as the address assignment method, enter the vpn-addr-assign command with the aaa argument:
Step 2 To establish the tunnel group called firstgroup as a remote access or LAN-to-LAN tunnel group, enter the tunnel-group command with the type keyword. The following example configures a remote access tunnel group.
Step 3 To enter general-attributes configuration mode, which lets you define a AAA server group for the tunnel group called firstgroup, enter the tunnel-group command with the general-attributes argument.
Step 4 To specify the AAA server group to use for authentication, enter the authentication-server-group command.
This command has more arguments that this example includes. For more information, see the command reference.
Configuring DHCP Addressing
To use DHCP to assign addresses for VPN clients, you must first configure a DHCP server and the range of IP addresses that the DHCP server can use. Then you define the DHCP server on a connection profile basis. Optionally, you can also define a DHCP network scope in the group policy associated with a connection profile or username. This is either an IP network number or IP Address that identifies to the DHCP server which pool of IP addresses to use.
The following configuration includes more steps than are necessary, in that previously you might have named and defined the connection profile type as remote access, and named and identified the group policy as internal or external. These steps appear in the following examples as a reminder that you have no access to subsequent tunnel-group and group-policy commands until you set these values.
Guidelines and Limitations
You can only use an IPv4 address to identify a DHCP server to assign client addresses.
Configuring DHCP Addressing Using the CLI
Configures IP address pools as the address assignment method. Enter the vpn-addr-assign command with the dhcp argument. See also Configuring IPv4 Address Assignments at the Command Line.
tunnel-group firstgroup type remote-access
Establishes the connection profile called firstgroup as a remote access connection profile.
Enter the tunnel-group command with the type keyword and remote-access argument.
tunnel-group firstgroup general-attributes
Enters the general-attributes configuration mode for the connection profile so that you can configure a DHCP server.
Enter the tunnel-group command with the general-attributes argument.
Defines the DHCP server by IPv4 address. You can not define a DHCP server by an IPv6 address. You can specify more than one DHCP server address for a connection profile.
Enter the dhcp-server command. This command will allow you to configure the ASA to send additional options to the specified DHCP servers when it is trying to get IP addresses for VPN clients. See the dhcp-server command in the Cisco Security Appliance Command Reference guide for more information.
The example configures a DHCP server at IP address 172.33.44.19.
Exit tunnel-group mode.
Enter the group-policy command with the internal argument to make an internal group policy.
The example configures an internal group.
(Optional) Enters group-policy attributes configuration mode, which lets you configure a subnetwork of IP addresses for the DHCP server to use.
Enter the group-policy command with the attributes keyword.
The example enters group policy attributes configuration mode for remotegroup group-policy.
The example configures a network scope of 192.86.0.0.
Note The dhcp-network-scope must be a routable IP address and not the subset of the DHCP pool. The DHCP server determines which subnet this IP address belongs to and assigns an IP address from that pool. Cisco recommends that you use an interface of the ASA as a dhcp-network-scope for routing reasons. You can use any IP address as the dhcp-network-scope, but it may require that static routes be added to the network.
Example
A summary of the configuration that these examples create follows:
Assigning IP Addresses to Local Users
Local user accounts can be configured to use a group policy, and some AnyConnect attributes can also be configured. These user accounts provide fallback if the other sources of IP address fail, so administrators will still have access.
This section describes how to configure all the attributes of a local user.
Prerequisites
User Edits
By default, the Inherit check box is checked for each setting on the Edit User Account screen, which means that the user account inherits the value of that setting from the default group policy, DfltGrpPolicy.
To override each setting, uncheck the Inherit check box, and enter a new value. The detailed steps that follow describe each of the settings on the Edit User Account screen.
Detailed Steps
The Edit User Account screen opens.
Step 4 Specify a group policy for the user. The user policy will inherit the attributes of this group policy. If there are other fields on this screen that are set to Inherit the configuration from the Default Group Policy, the attributes specified in this group policy will take precedence over those in the Default Group Policy.
Step 5 Specify which tunneling protocols are available for the user, or whether the value is inherited from the group policy. Check the desired Tunneling Protocols check boxes to choose the VPN tunneling protocols that are available for use. Only the selected protocols are available for use. The choices are as follows:
Note If no protocol is selected, an error message appears.
Step 6 Specify which filter (IPv4 or IPv6) to use, or whether to inherit the value from the group policy. Filters consist of rules that determine whether to allow or reject tunneled data packets coming through the ASA, based on criteria such as source address, destination address, and protocol. To configure filters and rules, choose Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Add/Edit > General > More Options > Filter.
Click Manage to display the ACL Manager pane, on which you can add, edit, and delete ACLs and ACEs.
Step 7 Specify whether to inherit the Connection Profile (tunnel group) lock or to use the selected tunnel group lock, if any. Selecting a specific lock restricts users to remote access through this group only. Tunnel Group Lock restricts users by checking if the group configured in the VPN client is the same as the users assigned group. If it is not, the ASA prevents the user from connecting. If the Inherit check box is not checked, the default value is None.
Step 8 Specify whether to inherit the Store Password on Client System setting from the group. Uncheck the Inherit check box to activate the Yes and No radio buttons. Click Yes to store the logon password on the client system (potentially a less-secure option). Click No (the default) to require the user to enter the password with each connection. For maximum security, we recommend that you not allow password storage.
Step 9 Specify an Access Hours policy to apply to this user, create a new access hours policy for the user, or leave the Inherit box checked. The default value is Inherit, or, if the Inherit check box is not checked, the default value is Unrestricted.
Click Manage to open the Add Time Range dialog box, in which you can specify a new set of access hours.
Step 10 Specify the number of simultaneous logons by the user. The Simultaneous logons parameter specifies the maximum number of simultaneous logons allowed for this user. The default value is 3. The minimum value is 0, which disables logon and prevents user access.
Note While there is no maximum limit, allowing several simultaneous connections could compromise security and affect performance.
Step 11 Specify the maximum connection time for the user connection time in minutes. At the end of this time, the system terminates the connection. The minimum is 1 minute, and the maximum is 2147483647 minutes (over 4000 years). To allow unlimited connection time, check the Unlimited check box (the default).
Step 12 Specify the Idle Timeout for the user in minutes. If there is no communication activity on the connection by this user in this period, the system terminates the connection. The minimum time is 1 minute, and the maximum time is 10080 minutes. This value does not apply to users of clientless SSL VPN connections.
Step 13 Configure the Session Alert Interval. If you uncheck the Inherit check box, the Default checkbox is checked automatically. This sets the session alert interval to 30 minutes. If you want to specify a new value, uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the minutes box.
Step 14 Configure the Idle Alert Interval. If you uncheck the Inherit check box, the Default checkbox is checked automatically. This sets the idle alert interval to 30 minutes. If you want to specify a new value, uncheck the Default check box and specify a session alert interval from 1 to 30 minutes in the minutes box.
Step 15 To set a dedicated IPv4 address for this user, enter an IPv4 address and subnet mask in the Dedicated IPv4 Address (Optional) area.
Step 16 To set a dedicated IPv6 address for this user, enter an IPv6 address with an IPv6 prefix in the Dedicated IPv6 Address (Optional) field. The IPv6 prefix indicates the subnet on which the IPv6 address resides.
The changes are saved to the running configuration.

